Reversing An ELF 32-Bit Executable: RE-1
TL;DR:
This was a pretty simple flag checker binary. I usedfile,strings, then popped it into Ghidra and the flag was basically spelled out in the decompiler.
1. Quick recon with file and
strings
First thing I do with these is check the file type and see if there’s any low-hanging fruit (like a flag sitting in plain text).
cyber@bun2:~/Stacksmash/RE$ file re-1
re-1: ELF 32-bit LSB pie executable, Intel i386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, BuildID[sha1]=b6619875228fde069ea88ae0f453f00e92fab0bc, for GNU/Linux 3.2.0, not stripped
cyber@bun2:~/Stacksmash/RE$ strings re-1 | grep flag
cyber@bun2:~/Stacksmash/RE$So yeah - I learned what I’m dealing with (32-bit ELF), but the grep didn’t return any immediate flags.
2. Opening the binary in Ghidra
Next, I opened it up in Ghidra and jumped straight to
main.
main.
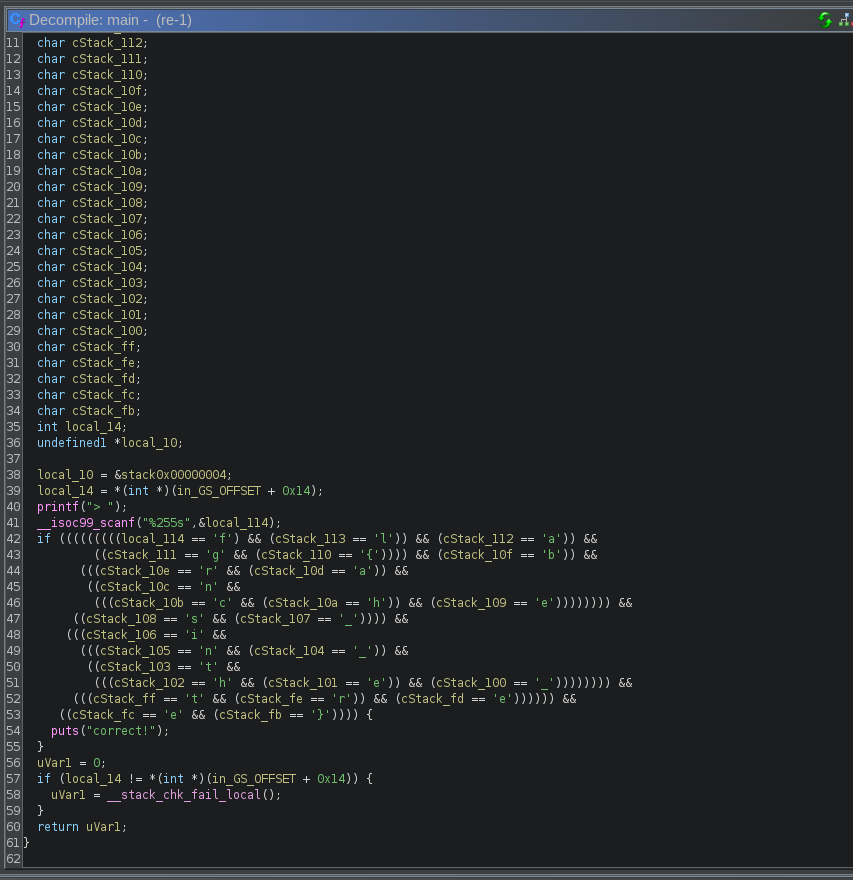
In the decompiled pane I immediately saw it printing a prompt:
printf("> ");
Then it reads user input with:
__isoc99_scanf("%255s", &local_114)
which means it reads up to 255 chars into a stack buffer.
main.
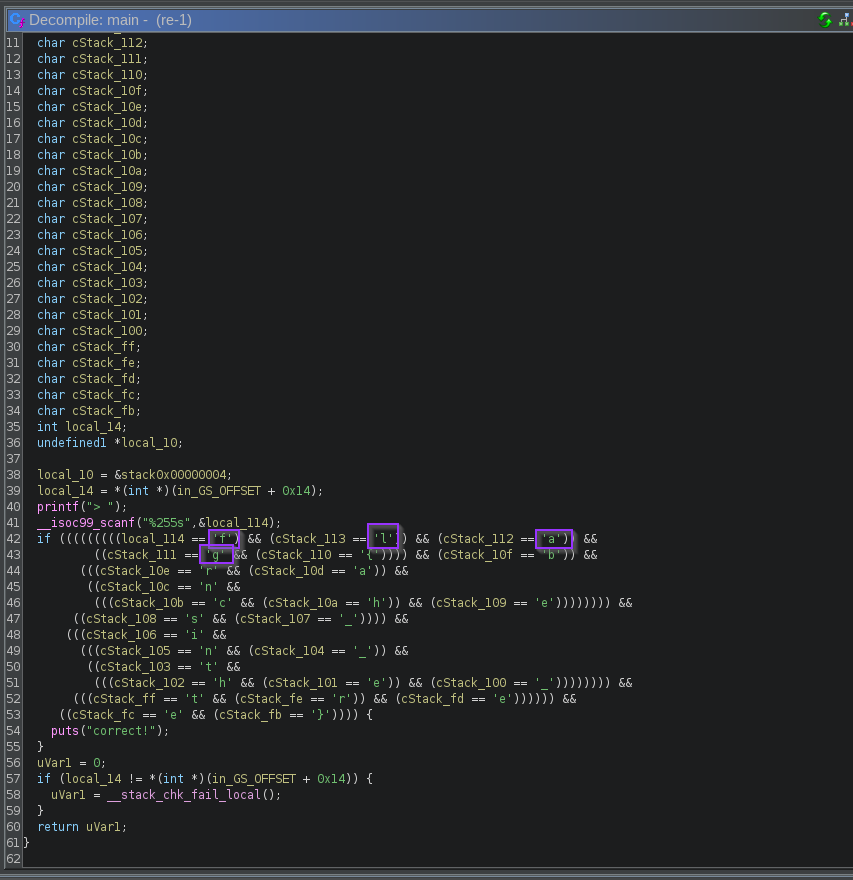
3. The flag was literally in the comparisons
After the input read, the program compares my input against a
hardcoded value, but it does it
one character at a time. Each
cStack_... is just the next byte in
that stack buffer.
And once you stare at it for a second, it’s basically spelling out: f l a g { b r a n c h e s _ i n _ t h e _ t r e e }
If every comparison matches, it prints a success message:
"correct!"
correct!.
4. Confirming by running the binary
At this point, I already knew the flag, but I ran the binary anyway just to confirm.
cyber@bun2:~/Stacksmash/RE$ ./re-1
> flag{branches_in_the_tree}
correct!
>Overall purpose
This function is a simple password-style flag checker. It prompts
for a single whitespace-delimited input string, then verifies it by
comparing each character against a hardcoded expected value (flag{branches_in_the_tree}). If the input matches exactly, it prints
correct! and exits normally.